Overview
Industrial Control Systems (ICS) and Operational Technology (OT) are vital elements of critical infrastructure, managing and automating industrial processes in industries such as energy, manufacturing, and utilities. These systems facilitate real-time monitoring and control of physical processes, which are crucial for maintaining operational efficiency, safety, and uninterrupted service. However, as ICS and OT systems become increasingly integrated with Information Technology (IT) networks and the broader digital landscape, they are exposed to an escalating risk of cyber threats. This increased connectivity introduces new vulnerabilities, making these systems more susceptible to cyberattacks that can disrupt operations and compromise safety.The Differences Between IT Security and ICS/OT Security
IT Security focuses on safeguarding information systems, networks, and data, with a primary emphasis on maintaining confidentiality, integrity, and availability (CIA) within enterprise environments. It protects corporate networks, servers, endpoints, and applications from various cyber threats, including hacking, malware, data breaches, and unauthorised access. Common IT security measures include firewalls, intrusion detection systems (IDS), encryption, access controls, and regular patching. IT systems are typically highly interconnected, which allows for rapid updates, patching, and centralised monitoring to respond quickly to emerging threats.
In contrast, ICS/OT Security is concerned with securing critical systems in industrial and operational settings, such as manufacturing plants, energy grids, transportation systems, and utilities. These systems control and manage physical processes, prioritising safety, availability, and reliability over data protection. ICS and OT environments often rely on specialised legacy systems that were not designed with cybersecurity in mind. The goal of ICS/OT security is to prevent physical damage to infrastructure, disruptions to critical services, or safety risks caused by cyberattacks. Unlike IT systems, OT systems typically operate on isolated or air-gapped networks, which makes real-time remote monitoring and patching more challenging. Additionally, minimising downtime in OT environments is crucial due to the potentially severe consequences, so the focus is on ensuring continuous operation with minimal disruption.
In summary, while both IT and ICS/OT security aim to protect systems, data, and operations, their focus, tools, and approaches differ. IT security concentrates on data protection and system integrity in interconnected environments, whereas ICS/OT security emphasises physical safety, reliability, and availability in often less connected environments, with an increased risk of physical damage.
Key differences between IT, OT, and ICS security:
| Aspect | IT Security | OT Security | ICS Security |
|---|---|---|---|
| Purpose | Protects data, networks, and IT systems | Protects physical devices, machines, and systems used in production and industrial processes | Protects control systems, Supervisory Control and Data Acquisition (SCADA) systems, and other devices critical to industrial operations |
| Scope | Focus on business systems, user data, and digital infrastructure | Focus on production, manufacturing, and automation systems | Focus on control systems in industries like energy, manufacturing, and utilities |
| Devices | Servers, computers, laptops, mobile devices, and network equipment | Sensors, Programmable Logic Controllers (PLCs), SCADA systems, and Human-Machine Interfaces (HMI) | SCADA systems, PLCs, Remote Terminal Units (RTUs), and ICS networks |
| Network Environment | Connected via corporate networks such as local area network (LAN), wide area network (WAN), and virtual private network (VPN) | Often isolated or segmented from IT networks | Often connected to isolated networks (air-gapped) or semi-connected to IT networks |
| Risk Focus | Data breaches, malware, ransomware, and unauthorised access | Physical damage to machines, downtime, and disruption of industrial operations | Cyberattacks targeting critical infrastructure, and physical safety hazards |
| Threat Landscape | Phishing, Distributed Denial-of-Service (DDoS) attack, ransomware, and insider threats | Malware, unauthorised device access, and system failure | Cyberattacks, espionage, and equipment failure |
| Availability Requirements | High availability, and minimal downtime expected | Continuous availability to avoid disrupting operations | Real-time operation, 24/7 availability critical to safety and operational continuity |
| Interdependency | Highly interdependent across systems and applications | Often operates in a siloed, independent manner with limited integration to IT | Often isolated but needs to interconnect with IT for monitoring, control, and automation |
| Cybersecurity Strategy | Primary focus on data protection, confidentiality, and integrity | Focus on ensuring safety, uptime, and integrity of industrial operations | Focus on securing critical infrastructure against disruptions and ensuring safe operations |
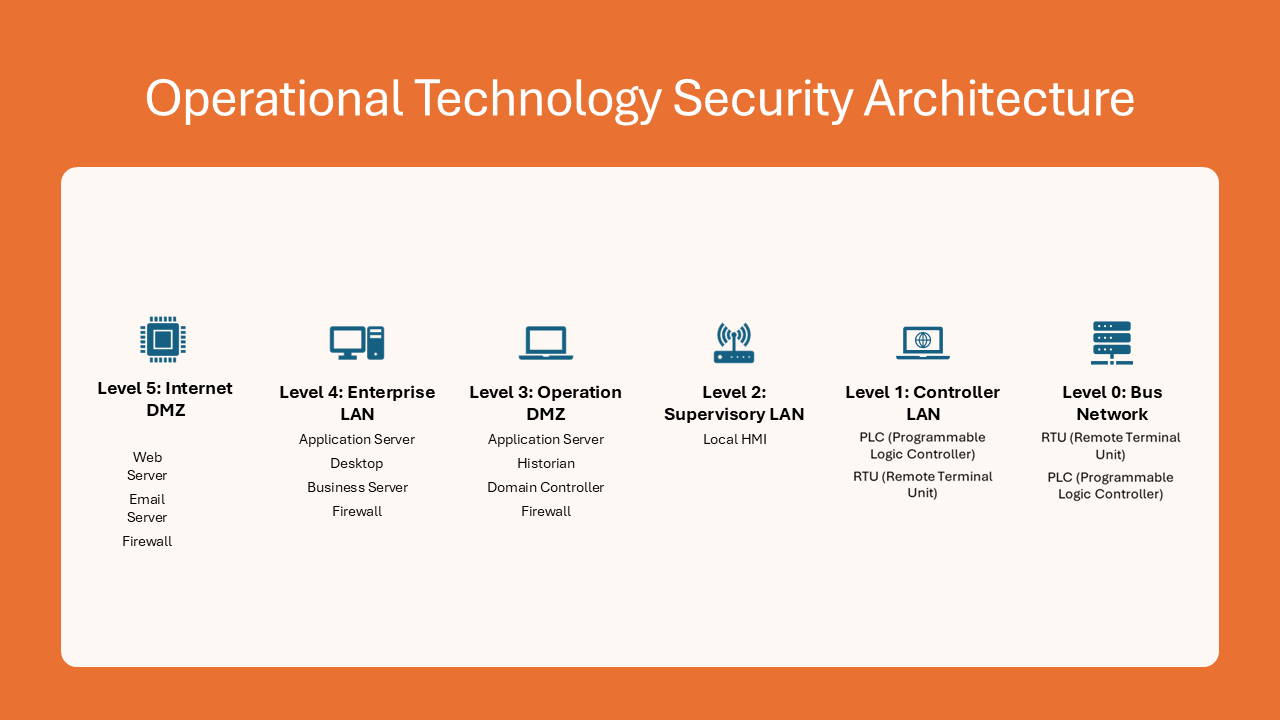 Figure 1: OT Security Architecture. Adapted from: https://www.paloaltonetworks.com/cyberpedia/ot-vs-ics-vs-scada-security
Figure 1: OT Security Architecture. Adapted from: https://www.paloaltonetworks.com/cyberpedia/ot-vs-ics-vs-scada-security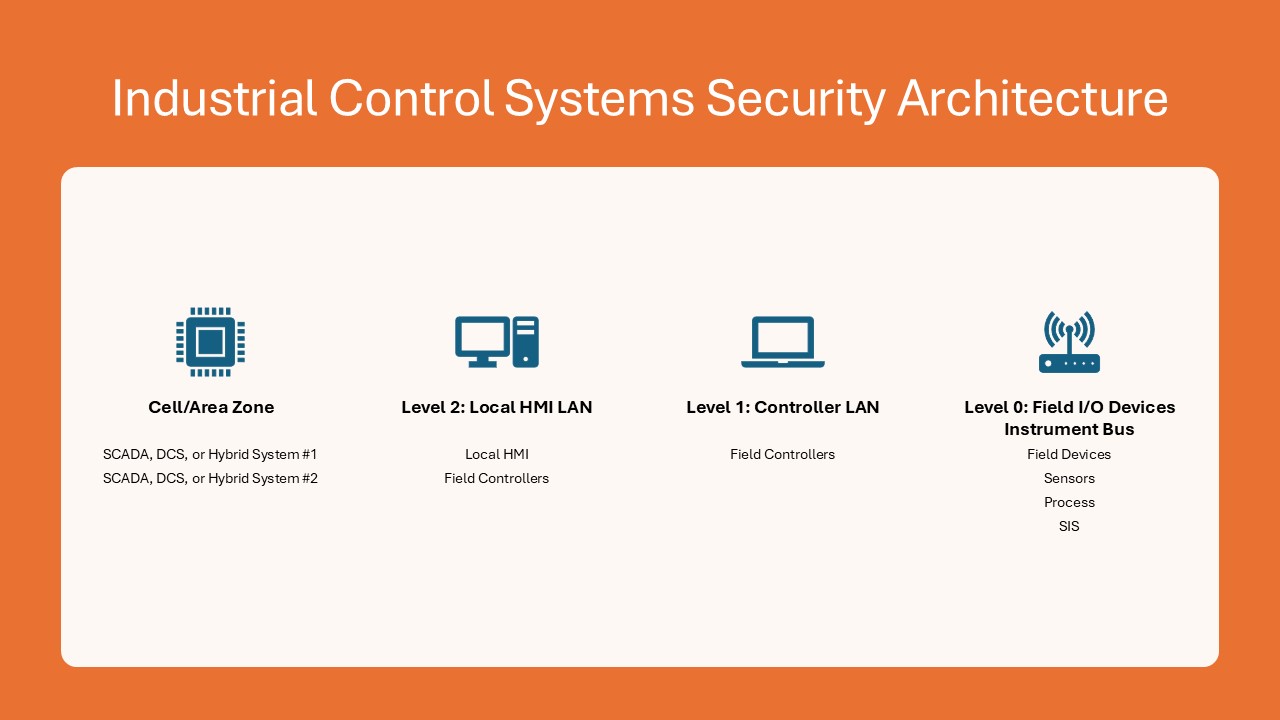 Figure 2: ICS Security Architecture. Adapted from: https://www.paloaltonetworks.com/cyberpedia/ot-vs-ics-vs-scada-security.
Figure 2: ICS Security Architecture. Adapted from: https://www.paloaltonetworks.com/cyberpedia/ot-vs-ics-vs-scada-security.Evolution of the ICS/OT Cybersecurity Threat Landscape
The cybersecurity threat landscape for Industrial Control Systems (ICS) and Operational Technology (OT) has undergone significant evolution in recent years, driven by the convergence of IT and OT environments, increased connectivity, and sophisticated attack tactics. As ICS and OT systems underpin critical infrastructure, these changes introduce new and complex risks. Below is an overview of the key trends and threats shaping the ICS/OT cybersecurity landscape:
- Increased Connectivity and the Rise of Industrial Internet of Things (IIoT): The expansion of internet-connected ICS/OT devices and their integration with corporate networks have drastically increased the attack surface. Hackers can exploit weak network segmentation or insecure remote access points, allowing them to infiltrate systems more easily. The convergence of IT and OT environments exacerbates this risk, allowing attackers to move laterally from IT vulnerabilities into OT systems, potentially disrupting critical operations.
- Advanced Persistent Threats (APTs): APTs targeting ICS/OT environments are often orchestrated by well-funded, highly skilled groups, including nation-state actors. These threats aim to steal intellectual property, disrupt operations, or cause physical damage. Increasingly, geopolitical motives drive cyberattacks, targeting critical industrial sectors such as energy, manufacturing, and transportation, raising the stakes for cybersecurity in these domains.
- Ransomware Attacks: Ransomware has become a growing concern in ICS/OT environments, where attackers lock critical systems or destroy data to extort ransom payments. High-profile incidents like the Colonial Pipeline attack highlight the severe operational disruptions ransomware can cause. In these attacks, criminals often exfiltrate sensitive data before encrypting it and threaten to release it unless a ransom is paid, adding an extra layer of pressure on organisations.
- Supply Chain Attacks: Cyberattacks targeting third-party vendors and suppliers, such as the SolarWinds breach, can have catastrophic effects on ICS/OT systems. Compromised software updates or hardware can provide attackers with a backdoor into critical infrastructure, escalating privileges and enabling further attacks. The introduction of insecure or backdoored devices can provide adversaries a foothold for the continued long-term access and exploitation of OT environments.
- Legacy Systems and Lack of Patching: Many ICS systems run on outdated hardware and software that cannot easily accommodate modern security patches or updates, leaving them vulnerable to cyberattacks. These systems often prioritise uptime over security. Manual patching practices result in prolonged exposure to known exploits.
- Cyber-Physical Threats: Some cyberattacks are specifically engineered to cause physical harm to industrial equipment or infrastructure. The 2010 Stuxnet attack on Iran’s nuclear facilities demonstrated the devastating potential of cyberattacks to sabotage industrial processes physically. Attacks on SCADA systems or PLCs can manipulate real-time operations, potentially leading to dangerous outcomes such as altering the flow of hazardous materials or disrupting power grids.
- IoT and Edge Device Vulnerabilities: Many IoT and edge devices in industrial settings often lack robust authentication mechanisms or end-to-end encryption, making them vulnerable to cyberattacks. Once compromised, these devices can be exploited to form botnets, such as the Mirai botnet, which launch DDoS attacks on critical ICS/OT systems, jeopardising their availability and disrupting operations.
- Use of AI and Machine Learning by Attackers: Cybercriminals are increasingly leveraging AI and machine learning to refine attack strategies, automate exploits, and evade traditional security defenses in ICS/OT environments. On the flip side, AI and machine learning are also being integrated into ICS/OT security to enhance intrusion and anomaly detection, enabling systems to identify potential threats based on behavioral patterns rather than known attack signatures.
- Lack of Visibility and Monitoring: ICS/OT environments often often lack real-time monitoring, making it challenging to detect and respond to attacks swiftly. Operational data is often siloed, and many OT systems were not designed with cybersecurity considerations. While ICS/OT-specific Security Information and Event Management (SIEM) solutions are emerging, many organisations still struggle with integrating IT and OT monitoring systems, which delays threat detection and response.
- Emerging Threats in Cloud and Hybrid Environments: The growing adoption of cloud computing and hybrid environments in industrial operations introduces new attack vectors. Misconfigurations in cloud services, insecure APIs, and vulnerabilities in edge computing devices create additional risks. Securing data flow between on-premise ICS systems and cloud-based services, as well as ensuring secure communication channels, remains a major cybersecurity concern in these evolving environments.
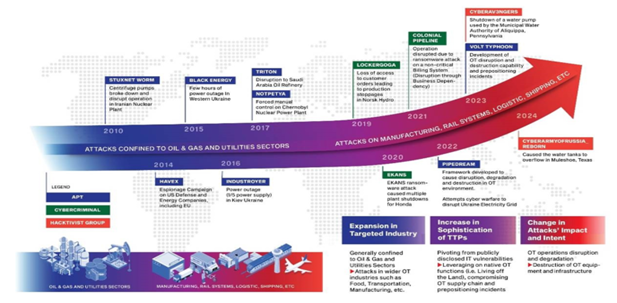 Figure 3: Attacks Against OT: Evolution And Escalation. Source: https://www.csa.gov.sg/Tips-Resource/publications/cybersense/2024/operational-technology-cybersecurity-threat-landscape-and-key-shifts.
Figure 3: Attacks Against OT: Evolution And Escalation. Source: https://www.csa.gov.sg/Tips-Resource/publications/cybersense/2024/operational-technology-cybersecurity-threat-landscape-and-key-shifts.The ICS/OT Security Challenges
Industrial Control Systems (ICS) and Operational Technology (OT) environments face several unique security challenges due to their reliance on legacy systems, the need for real-time operations, and the increasing convergence of IT and OT networks. Here are some of the top ICS/OT security challenges:
- Legacy Systems and Lack of Patching: Many ICS/OT systems operate on legacy hardware and software, often lacking support for modern security practices. These outdated systems may not be compatible with current security patches, making them vulnerable to exploitation. Attackers can exploit unpatched vulnerabilities, leading to unauthorised access or operational disruptions.
- Limited Visibility and Monitoring: ICS and OT networks often lack comprehensive monitoring tools, hindering real-time visibility and making it difficult to detect security incidents or anomalies. Without adequate monitoring, organisations struggle to identify threats, track malicious activities, and respond promptly to incidents.
- Convergence of IT and OT Networks: As IT and OT networks become increasingly interconnected, the attack surface expands. OT systems, once isolated, are now connected to the broader IT infrastructure, increasing their exposure to cyberattacks. Cyber threats targeting IT systems can easily spread to OT environments, disrupting critical infrastructure operations.
- Vulnerability Management: Identifying and addressing vulnerabilities in ICS and OT systems is challenging due to the specialised nature of these environments, which may require tailored detection and remediation tools. Exploiting these vulnerabilities can disrupt critical operations, especially in highly automated, real-time systems.
- Supply Chain Risks: ICS/OT systems rely on third-party suppliers and contractors for hardware, software, and services. Malicious actors can exploit vulnerabilities in the supply chain to infiltrate OT environments. Compromised supply chain components can introduce vulnerabilities or even deliberate backdoors into critical systems.
- Physical Security Concerns: ICS/OT environments, such as power plants and manufacturing facilities, contain physical components that must be secured against tampering, sabotage, or theft. Physical attacks can disable critical systems or create hazardous situations, posing severe operational risks.
- Ransomware and Malware Threats: ICS/OT environments are increasingly targeted by ransomware and malware. These attacks can lock down systems, disrupt operations, and demand ransom payments. Ransomware in OT environments can halt production processes, damage critical infrastructure, and result in severe financial and reputational consequences.
- Supply Chain Integration and Remote Access: The rise of remote access to OT systems, particularly for third-party maintenance or management, introduces additional risks associated with remote logins and communications. This expanded access increases the attack surface, making systems more vulnerable to cyber threats originating from outside the organisation.
The Importance of Cyber Security Assessment for ICS/OT Systems
Despite the numerous security challenges, conducting cybersecurity assessments for ICS and OT is essential due to their critical roles in industries such as manufacturing, energy, transportation, and utilities. The importance of conducting ICS/OT cybersecurity assessments stems from the following key factors:- Critical Infrastructure Protection: ICS and OT systems often control vital infrastructure that, if compromised, can have severe consequences on national security, public safety, and economic stability. For example, breaches in OT systems in power grids or water supply facilities can result in major disruptions, environmental damage, or even endanger lives. Therefore, assessing the security of these systems is crucial to identify vulnerabilities and mitigate risks before attacks can cause widespread harm.
- Integration of IT and OT: As IT and OT systems become increasingly interconnected in many modern environments, OT systems—traditionally isolated and less secure—are exposed to a broader range of cyber threats. This convergence necessitates a more integrated and proactive cybersecurity approach.
- Aging Infrastructure: Many ICS/OT systems are based on legacy technologies, which were not originally designed with cybersecurity in mind. These systems may still be running outdated software or hardware that cannot be easily patched or updated. A cybersecurity assessment can identify weaknesses related to outdated technologies, helping organisations prioritise upgrades or replacements before vulnerabilities are exploited.
- Increased Cyber Threats: ICS/OT systems have increasingly become targets for sophisticated cyberattacks from nation-state actors and cybercriminals. For instance, attacks like Stuxnet demonstrated the vulnerabilities of ICS/OT systems. Such threats are likely to evolve, requiring ongoing assessments to ensure defences are keeping pace with emerging attack techniques and evolving tactics.
- Regulatory Compliance and Standards: Governments and regulatory bodies are placing greater emphasis on cybersecurity in critical infrastructure. Many sectors have specific requirements and standards, such as the NIST Cybersecurity Framework or IEC 62443 that mandate regular cybersecurity assessments. Non-compliance can result in penalties, legal consequences, and reputational damage.
- Supply Chain Security: ICS/OT systems are increasingly dependent on third-party vendors and contractors, making supply chain security, including hardware, software, and service providers, is a growing concern. Cybersecurity assessments can uncover vulnerabilities not only within the systems but also in the extended supply chain, which could introduce new risks into the environment.
- Incident Detection and Response: ICS/OT environments often lack mature and robust incident detection and response mechanisms. Cybersecurity assessments help in establishing clear protocols for rapid detection, response, and recovery from cyber incidents. This reduces downtime, minimises impact, and ensures faster recovery in the event of a breach.
- Continuous Improvement: Cybersecurity is a constantly evolving field, and so are the cyber threats targeting ICS/OT systems. Regular security assessments help identify new risks, improve defence mechanisms, and ensure system resilience over time. They provide actionable insights for ongoing risk management, ensuring the organisation can adapt to changing security landscapes.
- Business Continuity: ICS/OT systems often play a critical role in business continuity, with even minor disruptions potentially leading to significant financial losses. Cybersecurity assessments identify gaps in risk management plans and ensure robust business continuity measures to minimise disruption and impact of cyber incidents.
Conclusion
Cybersecurity assessments for ICS/OT systems are essential for protecting critical infrastructure, ensuring operational continuity, and addressing evolving threats. These assessments help identify vulnerabilities in outdated systems, prevent cyberattacks, and ensure compliance with industry regulations. As IT and OT systems become increasingly integrated, such assessments help mitigate risks from new attack vectors, supply chain threats, and third-party vulnerabilities. By evaluating security measures, response preparedness, and recovery plans, cybersecurity assessments enable organisations to proactively safeguard their ICS/OT environments, minimising downtime, disruptions, and potential safety or financial consequences.References
- Singapore's Operational Technology Cybersecurity Masterplan 2024: https://www.csa.gov.sg/Tips-Resource/publications/2024/operational-technology-cybersecurity-masterplan-2024
- Operational Technology Cybersecurity Threat Landscape And Key Shifts: https://www.csa.gov.sg/Tips-Resource/publications/cybersense/2024/operational-technology-cybersecurity-threat-landscape-and-key-shifts
- Introduction to ICS/OT Systems and their Role in Critical Infrastructure: https://www.isaca.org/resources/news-and-trends/isaca-now blog/2023/introduction-to-ics-ot-systems-and-their-role-in-critical-infrastructure
- Industrial Control Systems: https://www.cisa.gov/topics/industrial-control-systems
- Threat Actors Continue to Exploit OT/ICS through Unsophisticated Means: https://www.cisa.gov/news-events/alerts/2024/09/25/threat-actors-continue-exploit-otics-through-unsophisticated-means
- SANS 2024 State of ICS/OT Cybersecurity: https://sansorg.egnyte.com/dl/5mD1Yxiybn